One question that comes up a lot in discussion is whether Linux is genuinely a faster OS when compared to Windows. Most of the questions direct us to the time it takes for the OSes to boot up and in that parameter, yes, Linux is noticeable faster than Windows. Why then, does it fail the speed test when compared along other parameters ?
Kernel
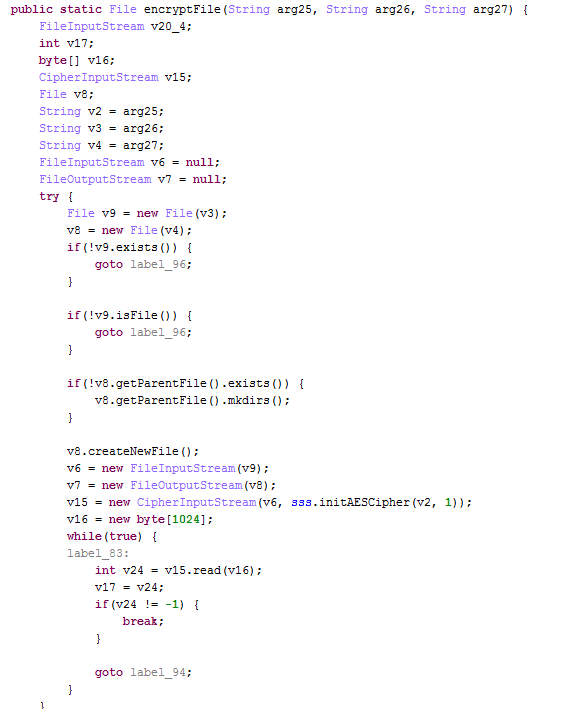
One big reason why Linux can boot up faster than Windows is the difference in the way their kernels are designed. The nucleus of an OS is very different in these 2 products. Linux has a monolithic kernel – meaning it holds every core functionality needed by the OS such as drivers ,memory management, task scheduler and the file system. Windows on the other hand contains a micro kernel which contains only the basic necessities and the remaining aspects are loaded separately thus making it a little bit slower when compared to Linux.
Backward Compatibility
This is one aspect wherein Windows suffers owing to the decades of software support it provides it’s users. While it may slow down the loading process, there’s no denying that a majority of the world’s computing needs require this compatibility. Linux on the other hand, being a minority shareholder in the computing world can afford to forgo backward compatibility.
While discussing this, we also need to note that Microsoft can afford for Windows to be slower for the simple reason that a potential user will not be dissuaded from purchasing a Windows license just because it works a little bit slower. Windows being a propriety OS has a limited number of developers and thus a finite number of man hours they can commit. Therefore, the development activities need to be market driven for Microsoft. Optimization is not as high a priority for Windows compared to other requirements.
Linux on the other hand outperforms Windows in many areas because it is essential for its existence.
Explanation From Tech-savvy Reddit user logicalkitten
- One of the more hidden benefits to linux is that applications share files better than windows. So instead of DLLs like in windows, linux uses .so files, or “shared objects”. There are also .ko files, which are kernel objects, somewhat like drivers in windows.
- A Windows application might depend on a very specific version of a DLL. The person who writes the application doesn’t know what version of windows you will be installing it on and if that particular DLL will be present in your system. So the easiest solution is to just include the correct DLL with the application. Effect: installers are much larger, C drive is fuller, and more ram is used.
- Linux does it differently. When you ask to install Midori web browser for instance, apt-get (or the software center front end) checks the package for a list of dependencies. Instead of including all the files, Midori just says what it depends on.
- So apt-get checks the system and sees that fileX.so.1 is already installed, which is one of the dependencies, so it doesn’t need to fetch it from the central software repository. It then notices that Midori needs another file, which is not installed yet, so it checks the software repository for a version that matches, or one that is newer. It installs that. And so on. Once the dependencies are satisfied, it installs the application itself. Result: Software can be installed very quickly and doesn’t take up as much space or ram.
- The apt-get system also keeps track of how many applications need fileX.so.1, so that if you remove Midori, it doesn’t remove fileX.so.1, unless nobody else is using it. So Linux has pretty good house keeping skills.
How many of the ardent Linux supporters would stick around if the OS starts having problems ?






 A gamer would be obviously aware of the Razer brand and true to their style they have released one of the best gaming keyboards available today. This keyboard comes with detachable wrist rest and also has 5 mechanical keys that can be customized for any action based on your choice. For those of you who love a backlit keyboard, this one comes with 16.8 million colours to choose from to satisfy those needs. To take it up a notch, the keys can be colored per-key or in an animated pattern of your choosing.
A gamer would be obviously aware of the Razer brand and true to their style they have released one of the best gaming keyboards available today. This keyboard comes with detachable wrist rest and also has 5 mechanical keys that can be customized for any action based on your choice. For those of you who love a backlit keyboard, this one comes with 16.8 million colours to choose from to satisfy those needs. To take it up a notch, the keys can be colored per-key or in an animated pattern of your choosing.
 After some time of a single minded dedication to making the best keyboards available irrespective of the price tag, Logitech has finally released a keyboard that will not suck your bank account dry. This keyboard sacrifices back light and custom macro keys for the affordable price tag, which might make it look a bit dull when compared to its peers but that is compensated by its magnesium-alloy skeleton. For a gamer who doesn’t care about bells and whistles, this should be in your short list.
After some time of a single minded dedication to making the best keyboards available irrespective of the price tag, Logitech has finally released a keyboard that will not suck your bank account dry. This keyboard sacrifices back light and custom macro keys for the affordable price tag, which might make it look a bit dull when compared to its peers but that is compensated by its magnesium-alloy skeleton. For a gamer who doesn’t care about bells and whistles, this should be in your short list. Like its predecessor in this list the SteelSeries Apex M500 also forgoes fancy bells and whistles for specialization. The keyboard lacks media keys and macros to come in a compact design. This keyboard is tailor made for fans of e-sports and a refreshing feel for the minimalist user.
Like its predecessor in this list the SteelSeries Apex M500 also forgoes fancy bells and whistles for specialization. The keyboard lacks media keys and macros to come in a compact design. This keyboard is tailor made for fans of e-sports and a refreshing feel for the minimalist user.