How to Access Deep Web and Dark Web?
Without the Internet in the present generation, our lives would have been incomplete. The Internet benefits us in many ways. Today in this article let us not discuss the pros of the Internet. Few of you might hear about Dark Web; we will make you understand what Dark Web is in this article.
There are so many things that are hidden regular internet use, by many secret agencies, large enterprises, and governments. Few of them are illegal. Before we tell you How to access the dark web? Look into different features.
The internet sites which we access in our daily life like Facebook, YouTube, Google and many other popular sites these are the surface internet (which are easily visible to any person). We can search the surface internet and access quickly with any search engine like Google, Bing, Yahoo, Yandex or any other popular browser like Chrome or Firefox.
They are few sites on the internet which are protected with passwords. No one can enter these sites without permission. These sites won’t be indexed by search engines because the bots cannot access these sites because of these sites are password protection.
Deep Web
Let us explain about Deep Web first before telling about the Dark Web. First, don’t get confused between Deep Web and Dark Web. These two are different ways of the internet we use. Deep Web is the password protected network protected by the Tor Servers.
In the deep web of the internet, you will be able to access the databases and secret(protected) files of government agencies, big business, and many other which are not helpful for a regular internet user to know.
These files and sites are protected that no-one can misuse the secret information. Tor Network protects this confidential information.
Want to access the deep web? Here it is how to do it:
First, If you want to access the deep web, you need a special URL. Special URL can be received from the agency or company for accessing the Deep Web. Without the URL and Password, no one can gain entree to the Deep Web.
This type of protection is helpful for the businesses who want to share their data across the globe but with limited persons deep web method help them a lot.
Dark Web
Dark Web is the deepest and unsafe part of the internet that anyone can reach. Dark Web is the place of the web where many illegal things like Drug Trading, Weapons, Human part trading, Arms Trading, Child Pornography, Hitman hiring, Credit card trading, Fraudulent passport and CitizenShips, Money Laundering and Counterfeiting happen.
Dark Web is the place for criminals, Black Hat Hackers, and Terrorists. If you access the Dark Web with your normal browsers like Chrome and Firefox, the hackers can trace you easily and steal your credit card or private information, and you will be in trouble.
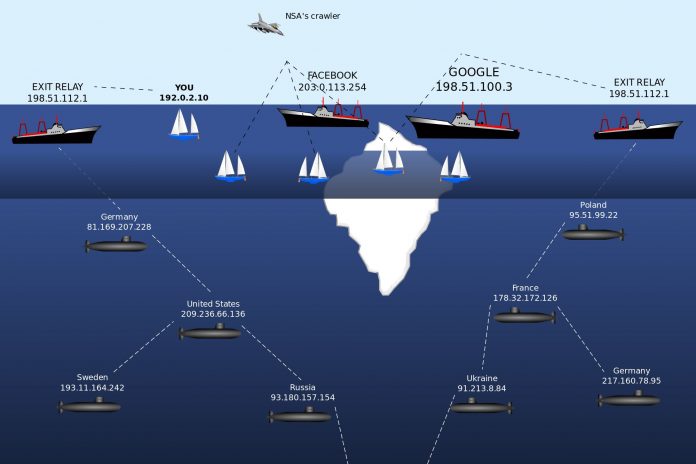
Accessing dark web is not easy because of the overlay networks. We require specific software and configurations or authorization to access the dark web.
The darknet which establishes the dark web includes small, friend-to-friend peer-to-peer networks, and as well as large, popular networks like Freenet, Tor, and I2P, operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnetdue to its unencrypted nature. The Tor dark web may be referred to as Onionland, a reference to the network’s top level domain suffix .onion and the traffic anonymization technique of onion routing.”
How to access Dark Web?
If you want to access the dark web, the first and foremost task to do is to download and install the Tor browser from the PC you want to access it. Go to the Security Settings page and then set the security level to high(no one can trace you while surfing Dark Web). Changing the settings makes your browser and PC little slow because it changes the IP in seconds so that you will be safe.
Note that the websites in Dark Web have a different URL from normal URL we use daily. Dark Web URLs most end with a .onion extension like, e.g., http://3g2upl4pq6kufc4m.onion/. http://3g2upl4pq6kufc4m.onion/ is the link to a popular search engine in Dark Web named as DuckDuckGo. DuckDuckGo search engine has a unique feature; the search engine never traces the users any data or the search history.
There are many secure search engines available apart of DuckDuckGo.DuckDuckGo is default search engine of TOR Browser.
After setting up everything the actual Dark Web is on Hidden Wiki, So read below to get the complete guide How to access the dark web?
The Hidden Wiki
The Hidden Wiki is the name of several censorship-resistant wikis operated by Tor hidden services. These are like regular Wikipedia pages anyone can anonymously edit it after registering on the site. The homepage works as a directory of links to other .onion sites like references. Just search Hidden Wiki on DuckDuckGo Search Engine from your TOR browser to access it. The first Four or Five links(depends) will not be the hidden wiki.
The first Hidden Wiki was operated through the .onion top-level domain which can be accessed only by using Tor or a Tor gateway.
The homepage provided by the community as a link directory to other hidden services like to offer contract killing, money laundering cyber-attacks for hire, contraband chemicals, bomb making and many other illegal things. The rest of the wiki was virtually uncensored as well and offer links to websites hosting child pornography and abuse images.
Did you know? The first iteration of the Hidden Wiki founded in October 2011, came to fame with its associations with illegal content. Before August 2013, the site was hosted on Freedom Hosting.
There are other hidden sites you can check with the help of the hidden wiki. The dark web is as big as surface web the more you check, the deeper you go. Please don’t click any of the suspicious links, because no one knows what is behind the link you clicked.
Warning: The article is written to provide knowledge about deep web and dark web. We don’t encourage or recommend it by any means. We are not responsible for any problem you get into or caused by you.